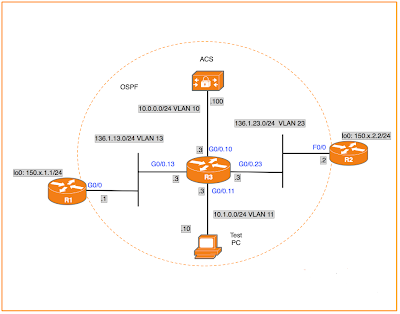
- Remove RIP from R1, R2, and R3.
- Configure Basic OSPF for all interfaces of R1, R2, and R3.
- Ensure that you have complete OSPF routes to all addresses in your network.
- Configure clear-text authentication between R1 and R3. Use the key cisco123clear.
- Configure strong authentication between R3 and R2. Use the key cisco123strong.
- On SW1, enable an SVI for VLAN 23.
- Assign an IP address to the process that resides on the assigned subnet.
- Enable OSPF for SW1.
- Ensure that SW1 receives routes to all destinations in the lab via OSPF.
- Enable strong authentication between R3 and SW1 using the key cisco321strong
R1 OSPF Configuration
R1>en
R1#conf t
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)#no router rip
R1(config)#router ospf 1
R1(config-router)#net 136.1.13.1 0.0.0.0 a 0
R1(config-router)#net 150.1.1.1 0.0.0.0 a 0
R2 OSPF Configuration
R2>en
R2#conf t
Enter configuration commands, one per line. End with CNTL/Z.
R2(config)#no router rip
R2(config)#router ospf 1
R2(config-router)#net 136.1.23.2 0.0.0.0 a 0
R2(config-router)#net 150.1.2.2 0.0.0.0 a 0
R2(config-router)#end
R3 OSPF Configuration
R3>en
R3#conf t
Enter configuration commands, one per line. End with CNTL/Z.
R3(config)#no router rip
R3(config)#router ospf 1
R3(config-router)#net 10.0.0.3 0.0.0.0 a 0
R3(config-router)#net 10.1.0.3 0.0.0.0 a 0
R3(config-router)#net 136.1.13.3 0.0.0.0 a 0
R3(config-router)#net 136.1.23.3 0.0.0.0 a 0
Verify that you are receiving all routes to the network.
R1 OSPF verification
R1#sh ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
+ - replicated route, % - next hop override
Gateway of last resort is not set
10.0.0.0/24 is subnetted, 2 subnets
O 10.0.0.0 [110/2] via 136.1.13.3, 00:09:21, GigabitEthernet0/0
O 10.1.0.0 [110/2] via 136.1.13.3, 00:09:21, GigabitEthernet0/0
136.1.0.0/16 is variably subnetted, 3 subnets, 2 masks
C 136.1.13.0/24 is directly connected, GigabitEthernet0/0
L 136.1.13.1/32 is directly connected, GigabitEthernet0/0
O 136.1.23.0/24 [110/2] via 136.1.13.3, 00:07:59, GigabitEthernet0/0
150.1.0.0/16 is variably subnetted, 3 subnets, 2 masks
C 150.1.1.0/24 is directly connected, Loopback0
L 150.1.1.1/32 is directly connected, Loopback0
O 150.1.2.2/32 [110/3] via 136.1.13.3, 00:07:49, GigabitEthernet0/0
R3 OSPF Verification
R3#sh ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
+ - replicated route, % - next hop override
Gateway of last resort is not set
10.0.0.0/8 is variably subnetted, 4 subnets, 2 masks
C 10.0.0.0/24 is directly connected, FastEthernet0/0.10
L 10.0.0.3/32 is directly connected, FastEthernet0/0.10
C 10.1.0.0/24 is directly connected, FastEthernet0/0.11
L 10.1.0.3/32 is directly connected, FastEthernet0/0.11
136.1.0.0/16 is variably subnetted, 4 subnets, 2 masks
C 136.1.13.0/24 is directly connected, FastEthernet0/0.13
L 136.1.13.3/32 is directly connected, FastEthernet0/0.13
C 136.1.23.0/24 is directly connected, FastEthernet0/0.23
L 136.1.23.3/32 is directly connected, FastEthernet0/0.23
150.1.0.0/32 is subnetted, 2 subnets
O 150.1.1.1 [110/2] via 136.1.13.1, 00:09:54, FastEthernet0/0.13
O 150.1.2.2 [110/2] via 136.1.23.2, 00:08:28, FastEthernet0/0.23
R2 OSPF Verification
R2#sh ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
+ - replicated route, % - next hop override
Gateway of last resort is not set
10.0.0.0/24 is subnetted, 2 subnets
O 10.0.0.0 [110/2] via 136.1.23.3, 00:08:54, GigabitEthernet0/0
O 10.1.0.0 [110/2] via 136.1.23.3, 00:08:54, GigabitEthernet0/0
136.1.0.0/16 is variably subnetted, 3 subnets, 2 masks
O 136.1.13.0/24 [110/2] via 136.1.23.3, 00:08:54, GigabitEthernet0/0
C 136.1.23.0/24 is directly connected, GigabitEthernet0/0
L 136.1.23.2/32 is directly connected, GigabitEthernet0/0
150.1.0.0/16 is variably subnetted, 3 subnets, 2 masks
O 150.1.1.1/32 [110/3] via 136.1.23.3, 00:08:55, GigabitEthernet0/0
C 150.1.2.0/24 is directly connected, Loopback0
L 150.1.2.2/32 is directly connected, Loopback0
Now that you know you are getting all the routes, configure the authentication between R1 and R3:
R1 and R3 Plain-text Authentication Configuration
On R1 the configuration is being performed at the interface level. You alternatively could configure
the authenticaion method for the area within the router process, however this is less granular than
the interface method. Additionally, all interfaces belonging to an area would then need
authenticaiton configured or they would loose ajacencies. The point here is that you need to be
aware of the effect of configuring the authentication method in the router process vs. the interface
level configuration.
R1#conf t
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)#int g0/0
R1(config-if)#ip ospf authentication
R1(config-if)#ip ospf authentication-key cisco123clear
% OSPF: Warning: The password/key will be truncated to 8 characters
Over on R3 you will have clear-text authentication for one interface and MD5 authentication on
another. This is not the place to configure authentication at the router process level as that would tie
one method to all interfaces of the area.
R3#conf t
Enter configuration commands, one per line. End with CNTL/Z.
R3(config)#interface f0/0.13
R3(config-subif)#ip ospf authentication
R3(config-subif)#ip ospf authentication-key cisco123clear
% OSPF: Warning: The password/key will be truncated to 8 characters
R3(config-subif)#end
R3#
R3#
*Jan 8 18:25:29.496: %OSPF-5-ADJCHG: Process 1, Nbr 150.1.1.1 on FastEthernet0/0
.13 from LOADING to FULL, Loading Done
*Jan 8 18:25:29.956: %SYS-5-CONFIG_I: Configured from console by console
R1 and R3 Plain-text Authentication Verification
First you'll notice the neighbors come back once authenticaion is configured for both R1 and R3.
Next, check to ensure you have routes:
R1#sh ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
+ - replicated route, % - next hop override
Gateway of last resort is not set
10.0.0.0/24 is subnetted, 2 subnets
O 10.0.0.0 [110/2] via 136.1.13.3, 00:03:02, GigabitEthernet0/0
O 10.1.0.0 [110/2] via 136.1.13.3, 00:03:02, GigabitEthernet0/0
136.1.0.0/16 is variably subnetted, 3 subnets, 2 masks
C 136.1.13.0/24 is directly connected, GigabitEthernet0/0
L 136.1.13.1/32 is directly connected, GigabitEthernet0/0
O 136.1.23.0/24 [110/2] via 136.1.13.3, 00:03:02, GigabitEthernet0/0
150.1.0.0/16 is variably subnetted, 3 subnets, 2 masks
C 150.1.1.0/24 is directly connected, Loopback0
L 150.1.1.1/32 is directly connected, Loopback0
O 150.1.2.2/32 [110/3] via 136.1.13.3, 00:03:02, GigabitEthernet0/0
You can see the authentication parameters in the ospf packet by issuing the debug ip ospf
packet command:
R1#debug ip ospf packet
OSPF packet debugging is on
R1#
Jan 8 19:04:31.336: OSPF-1 PAK : rcv. v:2 t:1 l:48 rid:136.1.23.3 aid:0.0.0.0 c
hk:8C8B aut:1 auk: from GigabitEthernet0/0
Jan 8 19:04:40.540: OSPF-1 PAK : rcv. v:2 t:1 l:48 rid:136.1.23.3 aid:0.0.0.0 c
hk:8C8B aut:1 auk: from GigabitEthernet0/0
In this case, the aut value of 1 indicates plain-text authentication, where an aut value of 0 would
indicate no authenticaiton.